Google spam policies offer assistance to ensure clients and move forward the quality of look that comes about. To be qualified to show up in Google web look comes about (web pages, pictures, recordings, news substances, or other fabric that Google finds over the web), the substance shouldn’t abuse Google Search’s by and large policies or spam policies recorded on this page. These arrangements apply to all web looks, counting those from Google’s claim properties.
Google identifies policy-violating substances and behaviors through mechanized frameworks and, as required, human audits that can result in manual activity. Locales that damage Google arrangements may rank lower in Comes About or not show up in Comes About at all.
If you accept that a location is damaging Google’s spam arrangements, let us know by recording a high-quality client report. Google is centered on creating adaptable and mechanized arrangements for issues, and Google will utilize these reports to advance the progress of Google spam location systems.
Google’s policies cover common shapes of spam, but Google may act against any spam it detects.
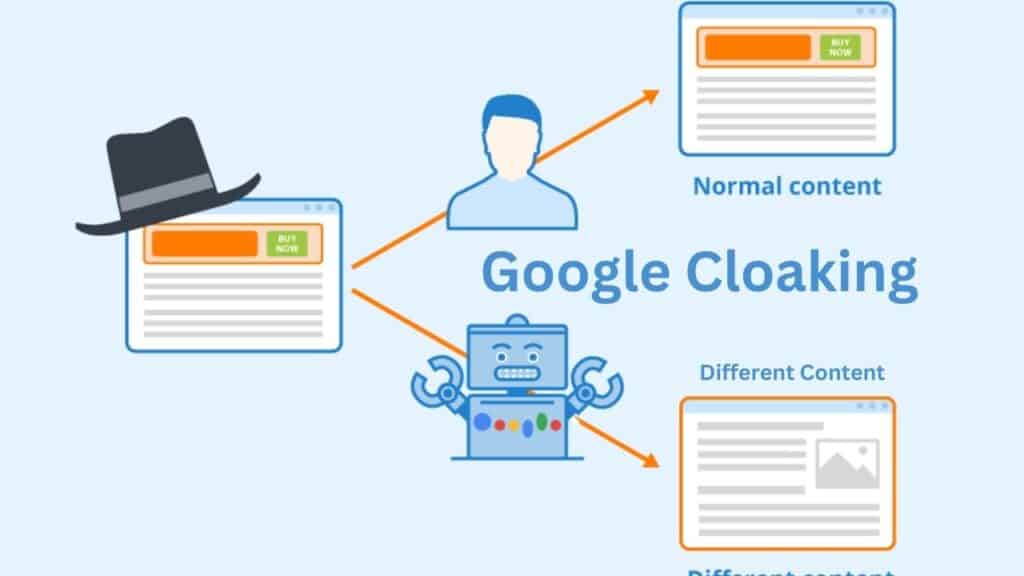
Cloaking
Cloaking alludes to displaying distinctive substance to clients and look motors with the expectation to control look rankings and deceive clients. Cases of cloaking include:
- Showing a page almost travel goals to look motors whereas appearing a page around rebate drugs to users
- Inserting Content or watchwords into a page, as it were, when the client specialist that is asking the page is a look motor, not a human visitor
If your location employment advances that look motors have trouble getting to, like JavaScript or pictures, see Google proposals for making that substance available to look motors and clients without cloaking.
If a location is hacked, it’s not exceptional for the programmer to utilize cloaking to make the hack harder for the location proprietor to identify. Studied approximately settling hacked destinations and maintaining a strategic distance from being hacked.
Work a paywall or a content-gating component.
Google does not consider this to be cloaking if Google can see the full substance of what’s behind the paywall like any individual who has got to to the gated fabric, and if you take after Google Adaptable Examining common guidance.

Doorways
Doorways are locales or pages made to rank for particular, comparable-looking questions. They lead clients to middle pages that are less valuable than the last goal. Illustrations of entryways include:
- Having numerous websites with slight varieties to the URL and domestic page to maximize their reach for any particular query
- Having different space names or pages focused on particular districts or cities that pipe clients to one page
- Pages produced to pipe guests into the real usable or important parcel of your site(s)
- Substantially comparable pages that are closer to look come about than a characterized, browsable hierarchy.
Expired Space Abuse
Expired space mishandling is where a terminated space title is obtained and repurposed fundamentally to control look rankings by facilitating substance that gives small to no esteem to clients. Illustrative cases incorporate, but are not constrained to:
- Affiliate substance on a location already utilized by a government agency
- Commercial therapeutic items being sold on a location already utilized by a non-profit restorative charity.
- Casino-related substance on a previous rudimentary school site
Hacked Content
Hacked substance is any substance set on a location without authorization due to site vulnerabilities. Hacked substance gives a destitute look comes about to Google clients and can introduce malevolent substances to their machines. Illustrations of hacking include:
- Code infusion: When programmers pick to get to your site, they might attempt to infuse noxious code into existing pages on your location. This frequently takes the frame of pernicious JavaScript infused specifically into the location or iframes.
- Page infusion: Sometimes, due to security flaws, programmers can include unused pages in your location that contain spammy or noxious substances. These pages are regularly implied to control look motors or to endeavor phishing. Your existing pages might not appear to be showing signs of hacking, but these newly created pages might hurt your site’s guests or your site’s execution in look results.
- Content infusion: Programmayeover attempts to control existing pages on your location quietly. Their objective is to include substance to your location that motors can see but may be harder for you and your clients to spot. This can include covered-up joins or Content to a page using CSS or HTML or more complex changes like cloaking.
- Redirects: Programmers might infuse pernicious code into your site, diverting a few clients to destructive or spammy pages. Sometimes, The divert depends on the referrer, client specialist, or gadget. For illustration, clicking a URL in Google looks to divert you to a suspicious page, but there is no divert when you visit the same URL specifically from a browser.
Here are Google tips on settling hacked locales and dodging being hacked:
Hidden Text And Links
Hidden Content or joins, is putting a substance on a page exclusively to control look motors and not to be effortlessly distinguishable by human guests. Illustrations of covered-up Content or joins that damage Google policies:
- Using white Content on a white background
- Hiding Content behind an image
- Using CSS to position Content off-screen
- Setting the textual style measure or mistiness to 0
- Hiding a connection as it was connecting one little character (for illustration, a hyphen in the center of a paragraph)
There are numerous web plan components nowadays that utilize appearing and covering up substance in an energetic way to progress client encounters; these components do not abuse Google policies:
- Accordion or selected substance that flips between covering up and appearing as extra Content
- Slideshow or slider that cycles between a few pictures or content paragraphs
- A tooltip or comparative Content that shows extra substance when clients connected with over an element
- Text that’s as it were, open to screen peruses and is aiming to move forward the encounter for those utilizing screen readers
Keyword Stuffing
Keyword stuffing alludes to the hone of filling a web page with watchwords or numbers to control rankings in Google Look. These watchwords frequently appear in a list or gather unnaturally or out of setting. Illustrations of catchphrase stuffing include:
- Lists of phone numbers without significant included value
- Blocks of Content that list cities and districts that a web page is attempting to rank for
- Repeating the same words or expressions so regularly that it sounds unnatural. For example:
Unlimited app store credit. Numerous locales claim to offer app store credit for $0, but they’re all fake and continuously mess up with clients looking for boundless app store credits. You can get boundless credits for the app store on this site. Visit the Google Boundless App Store credit page and get it today!
Link Spam
Google employees join as a figure in deciding the pertinence of web pages. Any joins that are aiming to control rankings in Google Look come about may be considered interface spam. This incorporates any behavior-controlling joins to your location or active joins from your location. The taking after is illustrations of interface spam:
- Buying or offering joins for positioning purposes. This includes:
- Exchanging cash for joins or posts that contain links
- Exchanging merchandise or administrations for links
- Sending somebody an item in trade for them, composing almost it, and counting a link
- Excessive interface trades (“Interface to me and I’ll interface to you”) or accomplice pages solely for cross-linking
- Using robotized programs or administrations to make joins to your site.
- Requiring an interface as a portion of a Terms of Benefit, contract, or comparative course of action without permitting a third-party substance proprietor the choice of qualifying the outbound link
- Text promotions or Content joins that do not piece positioning credit.
- Advertorials or local publicizing where installment is gotten for articles incorporating joins that pass positioning credit or joins with optimized grapple content in articles, visitor posts, or press discharges dispersed on other locales. For example:
There are numerous wedding rings on the showcase. If you are planning a wedding, you will have to choose the best ring. You will also need to purchase flowers and a wedding dress.
- Low-quality catalog or bookmark location links
- Keyword-rich, covered-up, or low-quality joins are implanted in widgets disseminated over different sites.
- Widely disseminated joins in the footers or layouts of different sites.
- Forum comments with optimized join in the post or signature, for example:
Thanks, that’s incredible info!
– Jhon
SEO Expert SEO Expert the best in Bd
- Creating low-value substances fundamentally to control connecting and positioning signals
Google understands that buying and offering joins is an ordinary portion of the web economy for publicizing and sponsorship purposes. It’s not an infringement of Google arrangements to have such joins as long as they are qualified with a rel=”nofollow” or rel=”sponsored” property esteem to the tag.

Machine-Generated Traffic
Machine-generated activity devours assets and meddles with Google’s capacity to serve clients best. Illustrations of robotized activity include:
- Sending computerized inquiries to Google
- Scraping comes about for rank-checking purposes or other mechanized get-to-Google Look conducted without express permission.
Such exercises abuse google spam arrangements and the Google Terms of Service.
Malware and Malevolent Behaviors
Google checks websites to see whether they have malware or undesirable computer programs that adversely influence the client experience.
Malware is any computer program or portable application intended to harm a computer, a portable gadget, its programs, or its clients. Malware exhibits evil behavior that can include installing computer programs without client consent and introducing destructive programs such as infections. Location proprietors sometimes do not realize that their downloadable records are considered malware, so these parallels might be inadvertently facilitated.
An unwanted program is an executable record or portable application that locks in misleading, startling behavior or influences the user’s browsing or computing involvement. Illustrations incorporate a program that switches your domestic page or other browser settings to ones you do not need or apps that spill private and individual data without legitimate disclosure.
Site proprietors ought to ensure that they do not damage the Undesirable Computer program Approach and follow Google guidelines.
Misleading Usefulness
Site proprietors ought to make websites with high-quality substance and valuable usefulness that benefits clients. Be that as it may, a few location proprietors proposed to control look positioning by intentioned making destinations with deluding usefulness and administrations that trap clients into considering they could get to a few substances or administrations but can not. Illustrations of deceiving usefulness include:
- A location with a fake generator that claims to give app store credit but doesn’t give the credit
- A location that claims to give certain usefulness (for case, PDF combine, commencement clock, online word reference benefit) but intentioned leads clients to beguiling advertisements or maybe giving the claimed services.
Scaled Substance Abuse
Scaled substance mishandling occurs when numerous pages are produced for the essential purpose of controlling look rankings and not making a difference to clients. This harmful practice is regularly centered on making huge amounts of predictable substance that gives little to no esteem to clients, no matter how it’s created.
Examples of scaled substance mishandling incorporate but are not restricted to:
- Using generative AI devices or other comparative apparatuses to produce numerous pages without including esteem for users
- Scraping nourishes looks come about, or other substances to create numerous pages (counting through computerized changes like synonymizing, interpreting, or other confusion strategies), where small esteem is given to users.
- Stitching or combining substance from diverse web pages without including value
- Creating different destinations to cover up the scaled nature of the Content
- Creating numerous pages where the substance makes small or no sense to a perused but contains look keywords
If you’re facilitating such substance on your location, avoid it from Search.
Scraped Content
Some location proprietors base their locales around substances taken (“scratched”) from other, regularly more legitimate locales. Scratched substance, indeed from tall quality sources, without extra valuable administrations or substance given by your location may not give included esteem to clients. It may, moreover, constitute copyright encroachment. A location may be downgraded if a critical number of substantial lawful expulsion demands have been gotten. Illustrations of injurious scratching include:
- Sites that duplicate and republish substance from other locales without including any unique substance or esteem, or indeed citing the unique source
- Sites that duplicate substance from other destinations alter it as it were (for example, by substituting equivalent words or utilizing robotized strategies) and republish it.
- Sites that replicate substance nourishes from other locales without giving a few sorts of special advantage to the user
- Sites devoted to inserting or compiling substance, such as recordings, pictures, or other media from other destinations, without considerable included esteem to the user
Sneaky Redirects
Redirecting is sending a guest to a URL different than the one they first requested. Slippery diverting is doing this maliciously in order to either make clients look at a distinctive substance or make clients startling substances that do not fulfill their unique needs. Illustrations of slippery diverts include:
- Showing look motors one sort of substance whereas diverting clients to something altogether different
- Showing desktop clients an ordinary page whereas diverting portable clients to a diverse spam domain
While subtle redirection is spam, there are numerous true blue, non-spam reasons to divert one URL to another. Illustrations of authentic diverts include:
- Moving your location to an unused address
- Consolidating a few pages into one
- Redirecting clients to an inside page once they are logged in
When looking at whether a divert is slippery, consider whether diverting is aiming to misdirect the clients or look at motors. Learn more about how to utilize fittingly diverts on your site.
Site Notoriety Abuse
Site notoriety mishandling is when third-party pages are distributed with small or no first-party oversight or inclusion, where the reason is to control look rankings by taking advantage of the first-party site’s positioning signals. Such third-party pages incorporate supported, promoting, accomplice, or other third-party pages that are regularly free of a have site’s primary reason or delivered without near oversight or inclusion of the have location and give small to no esteem to users.
Illustrative cases of location notoriety manhandling incorporate, but are not restricted to:
- An instructive location facilitates a page almost surveys of payday credits composed by a third party that disseminates the same page to other locales over the web, with the fundamental reason of controlling look rankings.
- A therapeutic location facilitating a third-party page, almost “best casinos” that’s planned essentially to control look rankings, with small to no inclusion from the stimulating site
- A motion picture survey location facilitating third-party pages approximately points that would be puzzling to clients to discover on a motion picture survey location (such as “ways to purchase devotees on social media locales,” the “best fortune-teller locales,” and the “best paper composing administrations”), where the reason is to control look rankings
- A sports location facilitating a page composed by a third party around “workout supplements audits,” where the sports site’s publication staff had small to no association with the substance, and the fundamental reason for facilitating the page is to control look rankings
- A new location facilitating coupons given by a third party with small to no oversight or association from the facilitating location, and where the fundamental reason is to control look rankings
If you’re facilitating pages that damage this approach, avoid that third-party substance from Look indexing.
Examples that are NOT considered location notoriety manhandle include:
- Wire benefit or press discharge benefit sites
- News distributions that have syndicated news substance from other news publications
- Sites outlined to permit user-generated substance, such as a gathering site or comment sections
- Columns, conclusion pieces, articles, and other work of a publication nature where there is near inclusion or survey by the site
- Third-party substance (for case, “advertorial” or “local promoting” sort pages) that’s delivered with the near association of the have location, where the reason is to share substance straightforwardly to peruses (such as through advancement inside the distribution itself), or maybe than facilitating the substance to control look rankings
- Embedding third-party advertisement units throughout a page or utilizing associate joins throughout a page, with joins treated appropriately.
- Coupons that are recorded with the near association of the facilitating site
Thin Associate Pages
Thin associate pages are pages with item associate joins on which the item depictions and audits are replicated straightforwardly from the unique dealer without any unique substance or included value.
Affiliate pages can be considered lean if they are a portion of a program that conveys its substance over an organization of partners without giving extra esteem. These locales frequently show up to be cookie-cutter destinations or layouts with the same or comparative substance imitated inside the same location or over numerous spaces or dialects. If a Look Comes About page returned a few of these locales with the same substance, lean member pages would make a disappointing client experience.
Not every location that participates in an associate program is a lean associate. Great associate destinations promote esteem by advertising important substances or highlights. Illustrations of great member pages incorporate advertising extra data about cost, unique item surveys, thorough testing and evaluations, routes of items or categories, and item comparisons.
User-generated spam
User-generated spam is a spammy substance included in a location by clients through a channel planning for client substance. Regularly, location proprietors need to be made aware of the spammy substance. Cases of spammy user-generated substance include:
- Spammy accounts for facilitating administrations that anybody can enlist for
- Spammy posts on gathering threads
- Comment spam on blogs.
- Spammy records transferred to record-facilitating platforms
Here are a few tips on how to avoid manhandling your site’s open regions. Here are Google tips on settling hacked locales and maintaining a strategic distance from being hacked.
Other Behaviors That Can Lead To Downgrade Or Removal
Legal Removals
When we get a large volume of substantial copyright expulsion demands, including a given location, google can utilize that to downgrade other substances from the location in Google. This way, if there is another encroaching substance, individuals are less likely to experience it versus the unique substance. Google applies comparable downgrade signals to complaints including criticism, fake merchandise, and court-ordered evacuations. In the case of child sexual mishandling fabric (CSAM), google continuously expels such substances when it is recognized, and Google downgrades all substances from locales with a large extent of CSAM content.
Personal data Removals
If Google handles a large volume of individual data evacuations including a location with exploitative evacuation hones, google downgrades other substances from the location in Google comes about. Google, too, to see if the same behavior design is happening with other destinations and, if so, apply demotions to substances in those locales. Google may apply comparative downgrade hones for destinations with many substance expulsions or non-consensual unequivocal symbolism removals.
Policy Circumvention
Suppose you lock in activities aiming to bypass Google spam arrangements or substance approaches for Google Look. In that case, google may take a suitable activity incorporating confining or evacuating qualifications for a few Google Look highlights (for case, Best Stories, Find). Circumvention incorporates but is not constrained to:
- Creating or utilizing numerous destinations with the purposeful of proceeding to damage Google policies
- Using other strategies planning to proceed dispersing substance or locks in behavior that points to abuse of Google policies
Scam and Fraud
Scam and extortion come in numerous shapes, including but not limited to mimicking official commerce or benefits through faker destinations, intentioned showing wrong data about a trade or benefit, or something else drawing in clients to a location on untrue pretenses. Utilizing mechanized frameworks, Google looks to distinguish pages with scummy or false substance and prevent them from appearing in Google Look comes about. Illustrations of online tricks and extortion include:
- Impersonating a well-known commerce or benefit supplier to trap clients into paying cash to the off-base party
- Creating beguiling locales imagining to give official client bolster for the sake of genuine commerce or give fake contact data of such commerce

